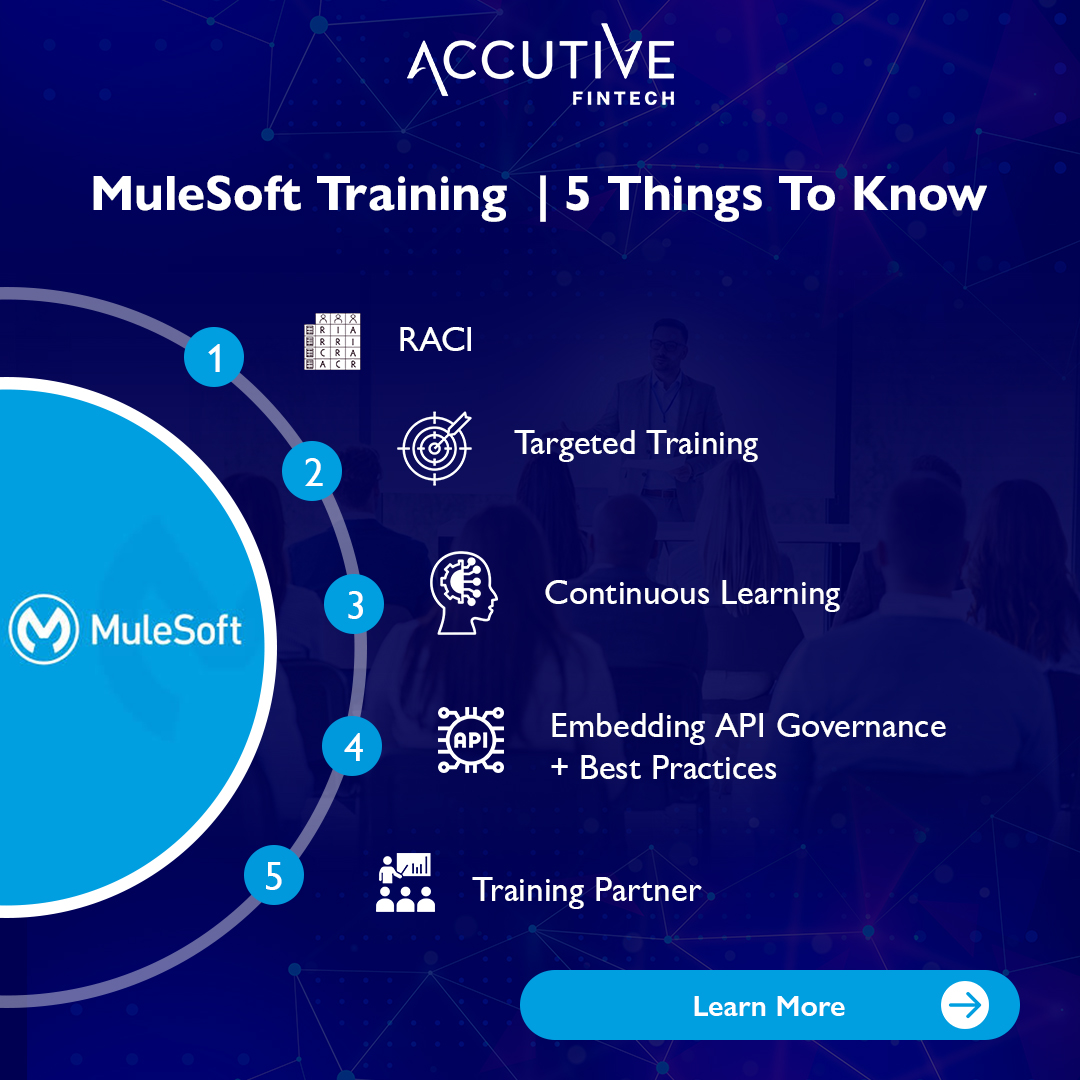
When it comes to training for MuleSoft or other iPaaS (Integration Platform as a Service) alternatives, there is no one
- Home
- FinTech Solutions
Most Recent Insights
4/23/24 Update: Salesforce has reportedly pulled out of the Informatica acquisition talks due to Informatica’s lack of interest in a
Is your financial institution navigating data integration challenges? MuleSoft Composer is your ally for seamlessly connecting various applications right within
Overview of Accutive FinTech’s services related to Temenos Journey Manager, a best-in-class digital customer onboarding platform that fully customize to your needs.
Overview of Accutive FinTech’s services related to MuleSoft, specialized to banks, credit unions, and other financial institutions.
Robotic Process Automation (RPA): what does it mean for banks? In the highly competitive and tightly regulated financial services landscape,
- Services
Explore Our Recent Case Studies
Learn how Accutive FinTech integrated a new digital payments platform with the core banking system and other applications using MuleSoft with zero defects
Explore how Accutive FinTech successfully completed a major loan origination system integration project with only 1 defect out of 200 test cases (0.5% defect rate).
Read how Accutive's quality obsessed approach is producing remarkably low defects in our latest Temenos Journey Manager project for a large regional bank.
- FinTech Insights
FinTech Insight Category
Case Studies
Whitepapers
Solution Briefs
Articles
- About Accutive
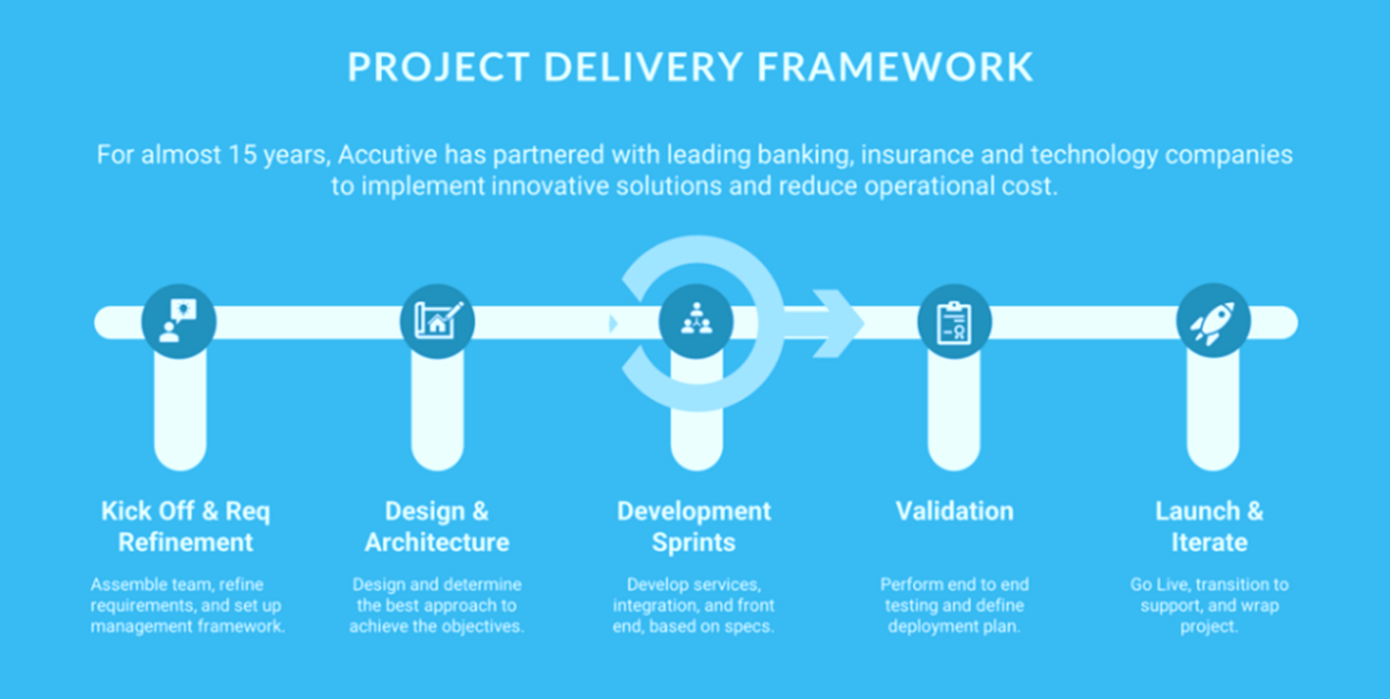
Accutive FinTech extends your team with experts who apply our Quality First Approach to deliver your digital transformation projects on time, on budget, and with low defects.
- Let’s Talk